Digital Signature & Digital Certificate
- Anand Nerurkar
- Sep 27, 2023
- 2 min read
Updated: Jul 1, 2024

Digital Signature Flow

How Digital Signature work
==
Digital Signatue make use of public key cryptography-Asymmetric key
In above example,
Bob-Sender make use of Asymetric key crptography and create public and private key. Bob keeps public key inpublic place from where Alice -Reciver can get key.
Now Bob want to send message say- Buy stock -10 quantity,price=400. Bob create a message digest code with hashing algorithm. This message digest is then further encypted by private key. This create some cipher text.
Now bob send this cipher text along with message to Alice-Receiver.
Now Alice-Receiver take public key, decrypt the cipher text to get message digest code. Alice use same hashing algorithm on plain message to create message digest code. This message digest code is then cmpared with message digest code she recived. if it match, then message is intact else message is modified in transit.
In this case, even digitial signature serve 3 puprose
-Identity (Authentication)
-Non-Repudiation
-Integrity
but does not verify identity. This is draback of digital signature. IT does not verify true identification and its public key.

So digital certificate along with difital signature is used.
Digital Certificate are electronic credential ,issued by Certificate of Authority. It not only verifies the identity ,but also owner own the public key. Digital certificate understand identity , does the verification by VerySign/globallySign with Certificate of Authority. This CA issue digital certificate with public key.
Now Bob attach his digital certificate along with his message-digitally singed.


How SSL Work
===



SSL/TLS handshake protocol
==
SSL/TLS are cryptographic protocol that provides security over the internet. This handshake protocol is used between client and server to establish trust and to negotiate what a secret key should be used to encrypt and decrypt the conversation.
With this protocol in place,eavesdroper can only see conenction endpoints,but can not read or modify any of the actual data,thus it protect data integrity and ensure safe transaction.
OSI model does the protocol operate

This handshake protocol is operating at top 3 layes of OSI model.
This is how request flow between client and server with handshake protocol

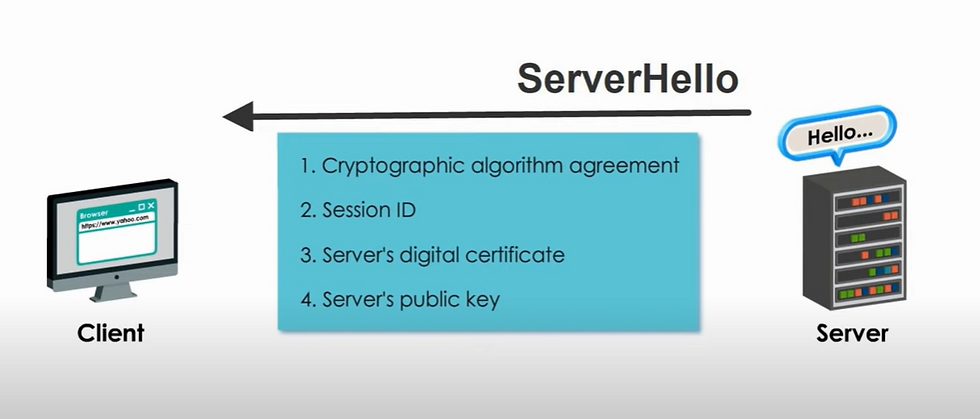
Client connect CA and verify digital certificate and thus establish trust.





-
.png)






Comments